Reporting, Dashboards & Metrics in UAE & Middle East
- Real-time security visibility across enterprise environments
- Executive-ready dashboards aligned to regional compliance frameworks
- Actionable SOC metrics that drive faster decisions
- Unified reporting across cloud, endpoints, network, and users

Choose the Best Cyber Security Company in Middle East
Choosing the best cybersecurity company in the Middle East means partnering with a provider that delivers continuous risk visibility, regional threat expertise, and enterprise-grade SOC capabilities.
Regional Threat Expertise
Enterprise-Grade SOC Capabilities
Our Core Services - What We Do
Security Operations Dashboards
We design centralized SOC dashboards that provide real-time visibility into threats, incidents, and response activities. Dashboards are customized for SOC analysts, CISOs, and IT leadership, ensuring rapid situational awareness and operational clarity across distributed enterprise environments.
Executive & Board-Level Reporting
Our executive reporting transforms complex security data into clear, risk-focused insights. Reports highlight threat trends, business impact, and security posture, enabling leadership teams to make informed decisions while maintaining alignment with organizational risk tolerance and regulatory obligations.
Incident & Response Metrics
We track and report critical SOC performance indicators including MTTD, MTTR, dwell time, and containment efficiency. These metrics help organizations measure response effectiveness, identify gaps, and continuously improve incident handling maturity.
Compliance & Regulatory Metrics
We deliver audit-ready metrics aligned with UAE and Middle East regulatory requirements. Our reports support frameworks such as ISO 27001, NCA, SAMA, and regional data protection mandates, simplifying audits while maintaining continuous compliance visibility.
Threat Intelligence Reporting
Our intelligence-driven reports correlate external threat data with internal telemetry. This provides context-rich insights into attacker behavior, active campaigns, and sector-specific risks, enabling proactive defense and prioritized mitigation actions.
Custom KPI & Risk Scorecards
We build tailored KPIs and risk scorecards mapped to business objectives. Metrics are aligned to assets, users, and critical processes, allowing organizations to quantify cyber risk, track improvement, and demonstrate measurable security value.
Explanation of Managed Security Device & Endpoint Services
Endpoint environments are primary targets for modern cyber attacks. SocEXpert’s endpoint-focused threat intelligence capabilities provide continuous visibility, contextual analysis, and proactive detection across enterprise devices.
Unified Endpoint Visibility
We provide consolidated visibility across desktops, laptops, servers, and mobile endpoints. Security telemetry is normalized into a single reporting layer, enabling SOC teams to quickly identify anomalous behavior, compromised assets, and policy deviations at scale.
Endpoint Threat & Incident Metrics
Our endpoint metrics track malware detections, exploit attempts, lateral movement indicators, and response actions. These insights allow teams to measure endpoint risk exposure, response efficiency, and overall endpoint security posture continuously.
Endpoint Compliance Reporting
We generate compliance-focused endpoint reports covering patch levels, configuration baselines, encryption status, and policy adherence. Reports support regulatory audits while helping security teams enforce consistent endpoint hygiene across the organization.
Performance & Health Dashboards
Endpoint performance dashboards monitor agent health, coverage gaps, telemetry flow, and sensor effectiveness. This ensures security tooling operates optimally without impacting business productivity or creating blind spots within the SOC environment.
Get Your Free Security Consultation
Best Security Solutions for Modern Network & SOC Challenges
SOCExperts helps organizations detect, assess, and respond to cyber threats with continuous monitoring, expert-led SOC operations, and proactive risk management.
Continuous Vulnerability Assessment vs Periodic Assessment
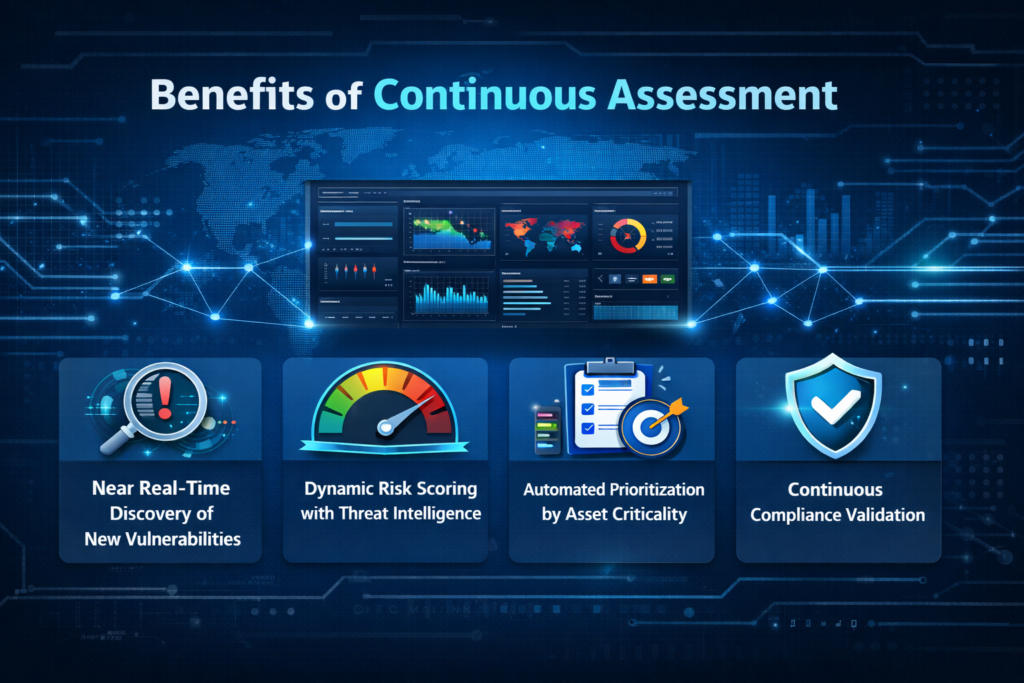
Limitations of Periodic Assessments
Traditional vulnerability assessments conducted quarterly or annually are no longer sufficient. In fast-moving enterprise environments, new vulnerabilities emerge daily, configurations change frequently, and threat actors exploit weaknesses within hours of disclosure.Periodic assessments often result in:
- Outdated risk views Backvisibility of unprioritized findings
- Limited visibility into real-world exploitability
- Compliance gaps between audit cycles
From Cyber Risk Chaos to Security Clarity
Traditional security approaches often slow organisations down and leave critical risks unaddressed. SOCEXpert transforms fragmented, reactive security efforts into a clear, continuous, and intelligence-driven vulnerability management approach, turning cyber risk into controlled, measurable outcomes.
The Problem
These represent what enterprises struggle with today
Disconnected & Inconsistent Security Reports
Security data is scattered across multiple tools, each generating separate reports with different formats and metrics. This lack of consistency makes it difficult for stakeholders to understand the overall security posture.
Static, Point-in-Time Reporting
Reports are generated periodically and reflect only historical data. This delayed visibility prevents organizations from understanding real-time risk exposure and emerging threat trends.
No Adversary Context
Security teams see alerts but lack insight into attacker intent, techniques, campaigns. Without adversary context, it becomes difficult to understand the true risk & prioritize response actions.
Manual Reporting & Data Compilation
Security teams spend excessive time manually collecting, normalizing, and preparing reports. This process is error-prone, resource-intensive, and diverts attention from active threat detection and response.
Lack of Actionable Metrics
Traditional dashboards focus on raw alert counts rather than meaningful security outcomes. Without actionable metrics, teams cannot accurately measure SOC effectiveness or prioritize improvements.
The Solution
Modern, continuous vulnerability management by SOCEXpert
Centralized Security Reporting Platform
All security data is consolidated into a single, unified reporting layer. Standardized reports provide consistent visibility across SOC operations, reducing complexity and improving decision-making.
Real-Time Dashboards & Continuous Metrics
Live dashboards provide real-time visibility into threats, incidents, and risk exposure. Organizations gain continuous situational awareness instead of relying on outdated, point-in-time reports.
Adversary-Focused Threat Context
Threat intelligence delivers deep insight into attacker tactics, techniques, and intent. Security teams gain clarity on who is attacking, how they operate, and what assets are at risk.
Automated Reporting & Data Normalization
Reporting workflows are fully automated, eliminating manual data compilation. This ensures accuracy, consistency, and timely delivery of insights while freeing SOC teams to focus on security operations.
Actionable, Outcome-Focused Metrics
Metrics focus on detection efficiency, response time, incident severity, and risk reduction. This enables organizations to measure SOC performance, identify gaps, and drive continuous improvement.
Tools, Technologies, and Methodologies
SocEXpert’s Threat Intelligence & Analysis services integrate seamlessly into existing enterprise security ecosystems, ensuring maximum value without operational disruption.
Centralized Security Reporting & Visibility
Reporting, Dashboards & Metrics provide unified visibility across security operations, cloud environments, applications, and endpoints. Security data is consolidated into structured reports that present incidents, trends, and risk exposure clearly, enabling leadership and SOC teams to understand the overall security posture without manual data aggregation.
Executive & Operational Dashboards
Role-based dashboards deliver real-time insights tailored for CISOs, security managers, and SOC analysts. Executives gain high-level risk and compliance views, while operational teams access detailed incident, alert, and performance metrics. This ensures informed decision-making, faster response prioritization, and alignment between security strategy and operations.
Security Metrics, KPIs & Compliance Tracking
Actionable metrics such as MTTD, MTTR, alert volumes, and incident severity are continuously tracked to measure security effectiveness. Compliance-aligned reporting supports audits and regulatory requirements by providing evidence-based metrics, trend analysis, and historical data, helping enterprises demonstrate control maturity and continuous improvement.
Compliance and Regulatory Relevance
SOCExpert aligns Security Architecture & Technology Management with global and regional compliance requirement
Benefits - Business Impact
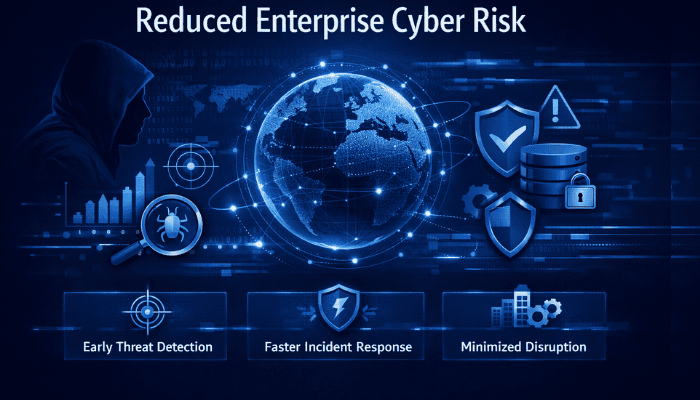
Executive-Level Visibility & Decision Support
Centralized reporting and real-time dashboards provide leadership with clear, actionable visibility into security posture, operational performance, and risk trends. Executives can quickly assess priorities, track KPIs, and make informed decisions backed by accurate, continuously updated metrics aligned with organizational objectives.
Improved Risk Management & Compliance Oversight
Structured metrics enable organizations to identify security gaps, monitor compliance status, and measure control effectiveness over time. Consistent reporting simplifies regulatory audits, supports evidence-based governance, and ensures risks are identified early, reducing exposure and strengthening compliance confidence across the enterprise.


Operational Efficiency & Performance Optimization
Automated dashboards eliminate manual reporting efforts and reduce data fragmentation across teams. By standardizing metrics and visualizing performance in real time, organizations improve operational efficiency, accelerate response times, and optimize resource allocation without increasing administrative overhead.
why choose us
socEXperts delivers reporting, dashboards, and metrics designed for security leaders who need clarity, accuracy, and decision-ready insights across complex environments.
- Purpose-built security dashboards that translate technical data into executive-level risk
- Real-time, centralized reporting that aligns security operations with governance
- Scalable metrics frameworks that adapt across cloud, endpoint, and application security environments.

FAQs
What is Threat Intelligence & Analysis in cybersecurity?
Threat Intelligence & Analysis is the process of collecting, correlating, and analyzing threat data to understand attacker behavior, intent, and risk. It enables enterprises to proactively detect threats, prioritize incidents, and strengthen security operations beyond reactive alert-based monitoring.
2. How does Threat Intelligence & Analysis improve enterprise security?
Threat Intelligence & Analysis improves enterprise security by providing context around threats, identifying active attack campaigns, and enabling early detection. This reduces attacker dwell time, strengthens incident response, and supports informed risk-based security decisions across complex environments.
3. Why is Threat Intelligence important for SOC operations?
Threat Intelligence is critical for SOC operations because it transforms raw alerts into actionable insights. It reduces false positives, improves alert prioritization, and enables analysts to understand attacker tactics, resulting in faster investigations and more effective incident response.
4. How is Threat Intelligence & Analysis different from traditional security monitoring?
Traditional monitoring focuses on reacting to alerts, while Threat Intelligence & Analysis emphasizes understanding attacker behavior and intent. Intelligence-driven monitoring enables proactive detection, contextual correlation, and continuous risk awareness rather than delayed, reactive incident handling.
5. What types of Threat Intelligence are used in enterprise environments?
Enterprise Threat Intelligence typically includes strategic, tactical, and operational intelligence. These layers support executive risk decisions, improve detection logic, and enhance real-time SOC investigations by aligning intelligence with assets, users, and business impact.
6. How does Threat Intelligence reduce false positives?
Threat Intelligence reduces false positives by correlating alerts with real-world attacker behavior and known threat patterns. This context allows SOC teams to distinguish genuine threats from benign activity, improving detection accuracy and analyst efficiency.
7. Is Threat Intelligence & Analysis relevant for UAE and Middle East enterprises?
Yes. Threat Intelligence & Analysis is highly relevant for UAE and Middle East enterprises due to region-specific threat actors, geopolitical risks, and regulatory requirements. Regional intelligence improves visibility into targeted campaigns and strengthens compliance readiness
8. How does Threat Intelligence support compliance and regulatory requirements?
Threat Intelligence supports compliance by strengthening monitoring, detection, and incident response controls required by regulations. It improves audit readiness, risk assessment, and continuous security monitoring aligned with standards such as ISO 27001 and regional cybersecurity frameworks.
9. Can Threat Intelligence integrate with existing SOC tools?
Yes. Threat Intelligence integrates with SIEM, EDR/XDR, and SOAR platforms to enhance correlation, detection, and response workflows. This ensures intelligence becomes operational rather than remaining static or disconnected from daily SOC activities.
10. What business benefits does Threat Intelligence & Analysis provide?
Threat Intelligence & Analysis reduces cyber risk, accelerates incident response, and improves SOC efficiency. By enabling proactive threat detection and informed decision-making, enterprises protect critical assets, minimize disruption, and optimize security investments without increasing operational overhead.